
picoCTF is an open-source project. It's an enhanced platform for education and organizing competitions in Cyber Security, Forensics, Cryptography, Web Exploitation and many other fields. This post will contain picoCTF challenges and solutions from Web Exploitation. If you are trying to sharpen your Cyber Security skills in the field of Web development, then you can learn a lot of stuff from this article.
However, I won't be providing any kind of files, scripts, or material regarding the challenge itself. For that, you can visit picoCTF Practice and page get the required material. This article is all about the explanation of these challenges and their solutions.
Keep in mind that there are multiple ways to solve any problem. So the solution provided for the particular challenge is just one way to solve it, there might be another way or perhaps the easy one. If so, do comment below.GET aHEAD
Find the flag being held on this server to get ahead of the competition
http://mercury.picoctf.net:15931/
This challenge is about web exploitation. The challenge involves reading and altering the request and response. A website link is given in the challenge and in that website there are two choices of red and blue. Selecting either of them changes the color of the body tag based on selection. The challenge is to find the flag being held on this server.
Solution:If you look at the source code of website, It's a simple template using Bootstrap CSS. No javascript or custom CSS stylesheet is attached in the HTML code. So it tells us there is no room for secrets or surprises. I tried all sorts of variations while selecting red and blue buttons but no luck. Then I come to realize that maybe the answer is in the request and response header itself. The second hint also verifies it while referring to the use of burpsuite.
Failed attempt:I have never used Burpsuite before this challenge. So I went to their website and somehow decided to use Dasterdly. It's their lightweight containerized application that scans web applications for security vulnerabilities. Going through the documentation, I found this command to check security vulnerabilities in the target website:
docker run --user $(id -u) --rm -v $(pwd):/dastardly -e DASTARDLY_TARGET_URL=http://mercury.picoctf.net:15931 -e DASTARDLY_OUTPUT_FILE=/dastardly/dastardly-report.xml public.ecr.aws/portswigger/dastardly:latest
By passing the challenge-given URL in the target URL, this docker command runs the container and scans the website for security. I checked the report but it did not point me anywhere. So, after the first setback, I decided to try a different approach which is to use the correct burp suite tool.
Succeed:I download and install Burp Suite Community Edition tool on Windows system. This tool is used to manipulate requests made to the server. It is actually the recommended tool by the second hint that I should have used in the first place.
Basic usage of Burp suite:- Open Burp Suite Community Edition, start a temporary project and select 'Proxy' from the options. While keeping the intercept off, click on 'Open browser' to launch the burp browser for testing.
-
Open the challenge website
http://mercury.picoctf.net:15931/in burp browser and turn on the intercept option. Now the request to the server will be held hostage by burp suite proxy and forwarded manually after analyzing or modifying the HTTP request. - Refresh the webpage and change HTTP request attributes as per need. Then click on forward to send the modified request to the server and see the response returned by the server by checking Network tab in inspect mode.
- We can also check response headers in the burp suite. After opening the burp suite temporary project, select option 'Target'. Select 'Open browser' to launch the burp browser and open any website. Burp suite target will capture that HTTP requests header. Send this captured request to 'Repeater' by right click and selecting 'Send to repeater'. Now select option 'Repeater' instead of 'Target' and modify the request headers. After altering the request, Send it to the server and inspect the response in 'Inspector' panel on the right.
Now while manipulating HTTP requests to the server, I tried almost all alternative values for headers and so far nothing turned out to be good. Then I realize that in the HTML code, there are two forms. Form handling the red color has 'GET' method while form handling the blue color has 'POST' method. In the challenge heading, It says GET aHEAD and it became all crystal clear.
I capture the HTTP request using burp suite, modify the method from POST to HEAD, and forward the modified HTTP request to the server. Now check the 'Response Headers' in 'Network' tab under 'Inspect' and you will find your flag:
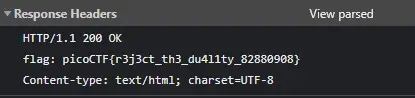
It worked for both Red and Blue form requests. Just make sure 'Network' tab is opened while forwarding the modified HTTP request to the server.
Alternate Solution:
Method 1: Now after understanding the challenge, I came up with an easy Python script that modify HTTP request header to get our flag. Just use the below script and It's done:
import requests url = 'http://mercury.picoctf.net:15931/' response = requests.head(url) print(response.headers)
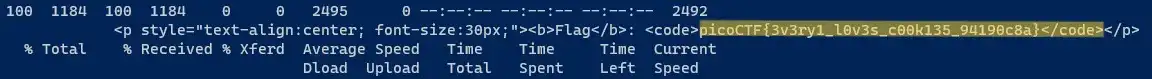
python3 script.py and you'll get the following output as shown in the image below that contains challenge flag.
 Now using this alternative, you can easily change HTTP request header and extract flag from
the server.
Now using this alternative, you can easily change HTTP request header and extract flag from
the server.
Method 2: If you want to make it super easy to check HTTP header request and grab flag, run this single command and the flag is yours:
curl -I HEAD http://mercury.picoctf.net:15931/
This linux command will output the HTTP header response that contains the flag. These are couple of methods that can be used to reveal the flag from the given challenge url.
Cookies
Who doesn't love cookies? Try to figure out the best one.
http://mercury.picoctf.net:21485/
This challenge is about cookies. Cookies are typically saved in our web browser and used for various purposes. There are actually several types of cookies and based on that, each type of cookie server different purpose. The best part is that we can specify cookies in HTTP request headers while making a custom request to the server. This challenge falls into this category.
Solution 1:Below is the Python script that can be used to get the flag but first you need to install bs4 and requests python pip pakages. Use the below command to install these required packages:
pip install requests beautifulsoup4
 Solution 2:
Solution 2:Instead of running a python script, you can also use this Bash script in Linux terminal to get the flag:
for i in {1..20};do curl -X GET -H "Cookie: name=$i" http://mercury.picoctf.net:21485/check;done | grep "<b>"
 Explanation:
Explanation:
We are given URL http://mercury.picoctf.net:21485/ and the challenge
is to find the flag in it. After running the URL in the browser, you'll notice that it takes
user input. The placeholder of input field is 'snickerdoodle' and if we search using
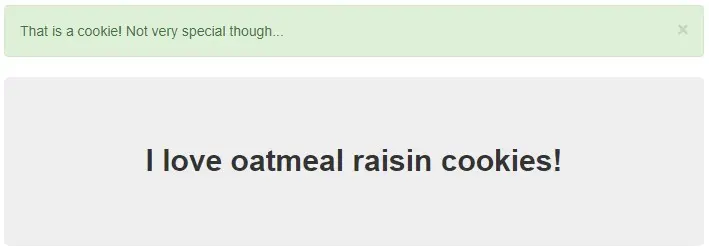
'snickerdoodle', we get the message saying 'I love snickerdoodle
cookies!' and an alert saying 'That is a cookie! Not very
special though...'.
Now there is no hint given in the challenge. But this placeholder is actually a hint itself. There is no HTTP cookies named 'snickerdoodle' but it's actually a real cookie that we eat. So the hint is to try eatable cookies in the search field. I did find two more cookies which are shortbread and biscotti. After trying them, I got the same message and alert. This means they are not the right cookie either.
There could be hundreds of eatable cookies and we simply can't find their names and try each
of them manually. So i opened http://mercury.picoctf.net:21485/ URL in Burp Browser using 'snickerdoodle' in the input field. While trying
to capture and modify cookies from the HTTP request header, I notice that after clicking on
search, two requests were made to the server. One is POST request to the PATH '/search' and
other one is GET request to PATH '/check'. In POST request headers, I changed the cookie
attribute from Cookie: name=-1 to
Cookie: name=1 and then forward the
request. After forwarding, burp captured the GET request. After changing the value from
Cookie: name=0 to Cookie: name=1 and forward the
request, I got this message:
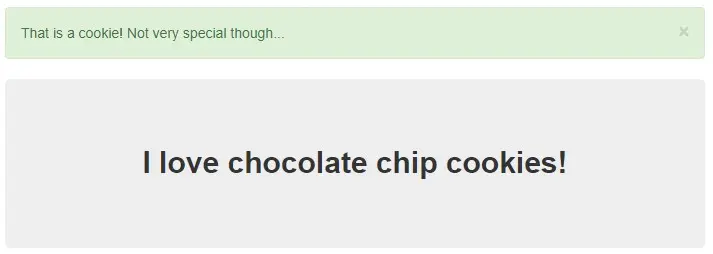
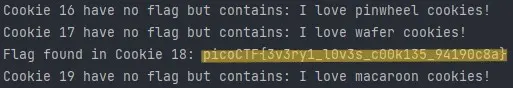
Now if you noticed, I input 'snickerdoodle' in the input field. Getting 'chocolate chip' instead of 'snickerdoodle' verifies that our HTTP request headers modification method works. But this cookie is also not the correct cookie. So I repeat the process and this time I used Cookie: name=2 in cookie modification. And I got this message:
Now we know the process to extract our flag from challenge website. We have to try each number in 'Cookie: name=' from 1 to until we get the flag. But It's not a good idea to manually modify cookies in HTTP request headers because we don't know how far we have to go. The flag might be at 'Cookie: name=50' or 'Cookie: name=70' and we cannot explore each number manually. I mean we can but It's not ideal to go through each number.
So to ease the process, I have written a Python script and Bash script. Use any script that you want. Both scripts iterate through numbers 1 to 20 while modifying the HTTP request headers and forwarding them to the server.
Insp3ct0r
Kishor Balan tipped us off that the following code may need inspection:
https://jupiter.challenges.picoctf.org/problem/9670/
orhttp://jupiter.challenges.picoctf.org:9670
This challenge provides two website links. Both links lead to the same server so you can use any link you want. The goal is same as always, find the flag. This challenge will be like 'walk in the park' for you if you know a little bit of inspecting in web browser.
SolutionBelow is the Python and Bash script that can be used to extract the flag. For Python script, requests pip package is required. Use pip install requests command to install the package.
This challenge provides different types of URLs but they all lead to the same server. We will be using URL http://jupiter.challenges.picoctf.org:9670 and the
challenge is to find the flag in it. After running the URL in the browser, you'll notice that it only
has two options: What and How. The heading of webpage says:
Inspect me and that's what need to do.
The flag for this challenge is scattered in three parts. This webpage is constructed with HTML, CSS, And JS files.
- First part of flag is inside the HTML file. Right-click on webpage and select 'View Page Source' and you can the first part of flag at the bottom of HTML page.
- Second part of the flag is in the CSS file. Add '/mycss.css' at the end of URL to see CSS file content in the browser. And you can find the second part of flag at the bottom of CSS file.
- Third part of the flag is in the JS file. Add '/myjs.js' at the end of URL to see Javascript file content in the browser. And you can find the third and final part of flag at the bottom of JS file.
Combine these parts into a single line and that's your flag: picoCTF{tru3_d3t3ct1ve_0r_ju5t_lucky?2e7b23e3}
Scavenger Hunt
There is some interesting information hidden around this site
http://mercury.picoctf.net:27393/
Can you find it?
This challenge is somewhat similar to the previous one but a little bit confusing because it explores different OS. A link is give and the task is to find the flag.
Solution: Use this Bash script to extract the flag: Explanation:This challenge provides a URL that gives information about It's usage of HTML, CSS, and JS. The flag is scattered in five parts. Just like previous challenge, you need to 'View Page Source' these pages and files to access the particular part of flag.
- Flag part 1: First part of flag is in the HTML file. 'View Page Source' the homepage and you will get the flag part at the bottom of the page.
- Flag part 2:
Second part of flag is in the CSS file. By going to
http://mercury.picoctf.net:27393/mycss.css, we can get the flag part at the botton of CSS file. - Flag part 3:
For third part, take a look at the JS file. By going to
http://mercury.picoctf.net:27393/myjs.js, you will get hint for the next part of flag. Basically the hint points towards robots.txt file. This file specifies the rules for web crawlers and instructs web crawlers to access or not access a certain webpage. By going tohttp://mercury.picoctf.net:27393/robots.txt, we can get the flag part from the robots file. - Flag part 4:
In the robots file, you'll get another hint for the next part of flag. It point
towards .htaccess file, which is a per-directory
configuration file for Apache web server that is used to override server settings in
the context of a specific directory. By going to
http://mercury.picoctf.net:27393/.htaccess, we can get the flag part from the .htaccess file. - Flag part 5:
For the last part, hint points towards the MAC. And due to my interaction with MAC,
I could not find the solution. So the credit for last part of flag goes to this Github Article. It turns out that MAC has hidden .DS_Store file in each directory that contains
custom attributes of icons, metadata, etc. This file can also be copied to the
server while transferring website files from the local server to the remote server.
So basically, by going to
http://mercury.picoctf.net:27393/.DS_Store,we can get the final part of flag.
Combine all the five parts and you will get your flag: picoCTF{th4ts_4_l03s_2_lO0k_d375c750}. You can also
use the Bash script provided above to automate the process
of extracting and combining flag from all different pages and files.
Some Assembly Required 1
http://mercury.picoctf.net:15472/index.html
This challenge does not provide any description. Just a link and the goal is same as always, to find the flag.
Solution: In Linux, run the below command to get the flag.curl -sS http://mercury.picoctf.net:15472/JIFxzHyW8W|grep -a pico
This challenge does not provide any hint or description. After opening the link, there is not much going on except the input box and submit button. If you 'Inspect' the webpage and under 'Network' tab, there are three files.
The first one is the index.html file, second is the Javascript file, and third file comes under suspicion because It's not being used anywhere. After Preview this file, you'll know that It's a binary file.
You can find the flag at the bottom of this file. picoCTF{c733fda95299a16681f37b3ff09f901c} is the flag for this challenge.
More Cookies
I forgot Cookies can Be modified Client-side, so now I decided to encrypt them!
http://mercury.picoctf.net:56136/
This challenge is a little bit tricky. The link provided in the challenge leads to a webpage that can only reveal flag if the user is an admin. But there is not login form. This webpage uses cookies to consider the user a normal user or an admin. We just need to find the appropriate admin cookies.
Solution: Below is the Python script that can be used to guess the correct cookies and reveal the flag: Explanation:This challenge is all about finding the right cookies. If you look at the first hint, It's about Homomorphic Encryption which is a cryptography technique that allows computations to be performed of the encrypted data without decrypting it and the result of that computations will also be in encrypted form. There are three types of Homomorphic Encryption schemes: Partially Homomorphic Encryption, Somewhat Homomorphic Encryption, and Fully Homomorphic Encryption.
In the challenge description: I forgot Cookies can Be modified Client-side, so now I decided to encrypt them!, letter C and B are capitalized which means they hint towards something. Turns out there is an mode of operation used in encryption named Cipher Block Chaining (CBC). In our case, it looks like CBC is used to encrypt block of data under partially homomorphic encryption scheme.
After some reading about CBC, you might find that It's vulnerable to Bit-flipping attack. You can use above Python script to reveal the flag. Below is the explanation of that code:
- First, we grab the cookies from the webpage and then decode the cookie to Its binary representation using base64. Then further decode the decoded cookie using base64 to turn it into bytes form.
-
In function, exploit, two 'for' loops are performed.
To revise the basics, every byte have 8 bits. So the first loop will select a byte
and second loop will flip the bit from the selected byte, by 8 times. Every time a
bit is flipped, a new encrypted cookie is constructed and a request is made to
http://mercury.picoctf.net:56136/using that cookie to check if that's the correct admin cookie. - If that constructed cookie is the correct admin cookie, It'll reveal the flag. Otherwise, loop will continue to the last byte until flag is revealed.
- The constructed cookie will only change a single byte at a time. Bytes before and after that changed byte remain the same.
In the end, you'll see a similar message where you can see the flag picoCTF{cO0ki3s_yum_e491c430}. It also shows which
byte was carrying the admin bit that we flipped and the constructed cookie.
Admin bit found in byte 9 bit 0
Flipped bit worked: b'o\xc7I\xbc\x12\rx\x08\xba\xcc'
Constructed cookie: YjhkSnZCSU5lQWk2ektSTDB5OVNoTzNYWHU5d2tHNUhUK2VmRmY2ZlhWWE92aTlrU1JKcy8vTStyTVhJVGxackRNZTFRUTkxTHFnR1NvYzFxMVdrakJ0S0oyZEdFMkZ3VXJIVFdoWUtJMk9YR0QwUDNla3l2N3VZTXl5MUlFemo=
Flag: picoCTF{cO0ki3s_yum_e491c430}
You can use the Client-side request modification application and use this constructed cookie
to get the flag.
where are the robots
Can you find the robots?
https://jupiter.challenges.picoctf.org/problem/56830/
or http://jupiter.challenges.picoctf.org:56830
curl http://jupiter.challenges.picoctf.org:56830/1bb4c.html 2>/dev/null| grep flag
You can also run this Python script to reveal the flag from the given link in the challenge. You might need to install some pip packages first.
ExplanationThe challenge is all about spotting clues and paying attention to them. The challenge title is about robots and that's where you should look first. This
robots.txt file can be found at the root of website. So this
link https://jupiter.challenges.picoctf.org/problem/56830/robots.txt
leads to robots.txt file. This file contains a clue for the flag. A webpage /1bb4c.html is specified as disallowed for robots or search engine crawlers.
That's it. Go to this page https://jupiter.challenges.picoctf.org/problem/56830/1bb4c.html and you can get the flag picoCTF{ca1cu1at1ng_Mach1n3s_1bb4c} written in
cleartext.
logon
The factory is hiding things from all of its users. Can you login as Joe
and find what they've been looking at?
https://jupiter.challenges.picoctf.org/problem/44573/
or http://jupiter.challenges.picoctf.org:44573
curl -sS -X GET -H "Cookie: admin=True" http://jupiter.challenges.picoctf.org:44573/flag | grep -oP "(?<=<code>).*(?=<\/code>)"
Additionaly you can run this Python script to grab the flag from the challenge url. Just make sure to install the required pip packages.
ExplanationThe challenge is also about Cookie. Link provided in the challenge leads to a login page. We can log in using any username or password except Joe, as said in the description. We get an error while trying to log in as Joe using some random password. There's no way we can guess the password. Sure you can brute force it but without knowing anything about the structure of password, It will be just a blind shot.
So to get around it, we will use the same old technique of HTTP request header modification.
I'm using Burp Suite for the purpose but you can use any tool you like. Open the challenge link, login using any username/password, hold the HTTP header request, and modify
Cookie: admin=False to
Cookie: admin=True. Now
forward the modified request to the server. Similar request might come up several times, so
change the admin value for every request. After that, you will get the flag picoCTF{th3_c0nsp1r4cy_l1v3s_0c98aacc} in plaintext.
dont-use-client-side
Can you break into this super secure portal?
https://jupiter.challenges.picoctf.org/problem/17682/
or http://jupiter.challenges.picoctf.org:17682
After opening a link given in the challenge, It asks to input a password. The password is actually the flag. By checking the source code of webpage, we can see the logic behind verifying password in Javascript which is exposed in HTML file. The challenging part is that the flag is scattered in 8 parts and each part is checked for 4 characters individually each time we enter a character in the input field.
At first, I decided to brute force it using strings and selenium library in Python but then I realized that Javascript code in webpage only gives an error if the first four characters of user input are not 'pico'. After that, no matter what our input is, script does not give any error. So we go blind until we input the whole password or flag. And there is no way to verify if our next input character is the right character or not. So, no brute force.
What worked for me is regular expression
to search and grab the text between ' ' because all the
flag strings are inside single quotes. Then I append this text into a new
dictionary and construct a new string by combining the keys in a particular order. And here
it is, our flag: picoCTF{no_clients_plz_b706c5} in plaintext.
The logic was actually pretty simple. You see the source code of webpage and javascript code is exposed in the HTML file. So the logic is like this:
- Javascript code checks the user input password by dividing it into 8 parts and each part consists of 4 characters.
- Script only checks for the first four characters. If they are 'pico' then we can proceed further, otherwise, we will get an error. For ex: first part is 'pico' and the only way to get no error is to input all four characters 'pico' in the same order. If you reduce characters or shuffle the order, you will get an error.
- There is no way to check the next input characters after 'pico', whether they are true or not. Password verified alert only shows when we input the whole flag or password.
split = 4;
(0, split) == 'pico' as (0, 4) == 'pico' | (0, 4) == 'pico'
(split*6, split*7) == '706c' as (24,28) == '706c' | (4, 8) == 'CTF{'
(split, split*2) == 'CTF{' as (4, 8) == 'CTF{' | (8, 12) == 'no_c'
(split*4, split*5) == 'ts_p' as (16, 20) == 'ts_p' | (12, 16) == 'lien'
(split*3, split*4) == 'lien' as (12, 16) == 'lien' | (16, 20) == 'ts_p'
(split*5, split*6) == 'lz_b' as (20, 24) == 'lz_b' | (20, 24) == 'lz_b'
(split*2, split*3) == 'no_c' as (8, 12) == 'no_c' | (24,28) == '706c'
(split*7, split*8) == '5}' as (28, 32) == '5}' | (28, 32) == '5}'
# Multiply the split by 4 and then sort all the lines in ascending order
# (or you can say It's a table of 4). Combine the strings, that's our flag.
# picoCTF{no_clients_plz_b706c5}
Multiply was just for understanding, you can just sort these lines using numbers assigned to split.
Logic 2
split = 4;
(0, split) == 'pico' to (0, split) == 'pico'
(split*6, split*7) == '706c' to (split, split*2) == 'CTF{'
(split, split*2) == 'CTF{' to (split*2, split*3) == 'no_c'
(split*4, split*5) == 'ts_p' to (split*3, split*4) == 'lien'
(split*3, split*4) == 'lien' to (split*4, split*5) == 'ts_p'
(split*5, split*6) == 'lz_b' to (split*5, split*6) == 'lz_b'
(split*2, split*3) == 'no_c' to (split*6, split*7) == '706c'
(split*7, split*8) == '5}' to (split*7, split*8) == '5}'
# Instead of multiplying, we can just sort the script lines in ascending order
# as (0, split, split*2, split*3...split*7). Combine the strings, that's our flag.
# picoCTF{no_clients_plz_b706c5}
So, as per my understanding, that's the whole logic behind constructing the flag. The Python script that I provided is constructing the flag in a different manner, so do check it out also.
It is my Birthday
I sent out 2 invitations to all of my friends for my birthday! I'll know
if they get stolen because the two invites look similar, and they even have the same md5
hash, but they are slightly different! You wouldn't believe how long it took me to find
a collision. Anyway, see if you're invited by submitting 2 PDFs to my website.
http://mercury.picoctf.net:20277/
https://github.com/grevutiu-gabriel/python-md5-collision
After cloning the repository, run python3 gen_coll_python.py command to run the
script. After the script, run the below command to rename files as PDFs:
mv out_py_good.py invite1.pdf && mv out_py_evil.py invite2.pdf
Now use or upload these PDF files to the challenge webpage to get the flag.
Explanation:As the description of this challenge says, both files have the same md5 hash but they are slightly different. md5 is vulnerable to collision attack and it's also acknowledged in the description as well. md5 collision is where two different files have the same md5 hash. To solve this challenge, we just need to create two pdf files with the same md5 hash while their content is slightly different from each other.
You can generate two files with the same md5 hash using the Python script provided above.
After generating files, run md5sum file1 file2 (replace file1 and file2 with
the names of files generated by python script) command to check their md5 hash. You will
notice that both files have the same md5 hash. You can also run
diff -q file1 file2 to check if both files are
similar or different. From the output, you can confirm that both files are slightly
different.
As required for the challenge, we now have two files that are slightly different but have
the same md5 hash. This is the flag that I extracted using this method:
picoCTF{c0ngr4ts_u_r_1nv1t3d_da36cc1b}
Who are you?
Let me in. Let me iiiiiiinnnnnnnnnnnnnnnnnnnn
http://mercury.picoctf.net:52362/
Below is the Python script that you can use to reveal the flag. Make sure to install requests and bs4 libraries in your python environment.
ExplanationWhen we access the URL provided in the challenge description, It leads to some kind of meme page where heading says: Only people who use the official PicoBrowser are allowed on this site!. This is the biggest hint itself. When a client (web browser) made request to the web server, User-Agent header is passed along with other information to the server via HTTP header. This header tag contains information of client browser. To solve this challenge we need to pass the request to the web server with custom HTTP header values.
I used python to make custom HTTP requests to the web server but you can use curl command on Linux terminal or inspect in browser itself to make altered HTTP requests.
- First pass
"User-Agent": "PicoBrowser"and make request to the web server. Altering this header value will make it look like that the request is originating from the PicoBrowser. -
If you check response from the web server, you will notice that there is a new
heading now that says: I don't
trust users visiting from another site. To overcome this issue, we
need to add Referer header
in our HTTP request. Add
"Referer": "http://mercury.picoctf.net:52362/"and make new HTTP request. -
After checking the response, there will be another message that says:
Sorry, this site only worked in
2018 which indicates that the HTTP request to the server must
originates from year 2018 in order to proceed further. We will add another
header Date that provides
the information about when the request was generated. Use
"Date": "Tue, 15 Nov 2018 12:45:26 GMTto set the date back in 2018 and make the request. -
After checking the response, there will be another message that says:
Sorry, this site only worked in
2018 which indicates that the HTTP request to the server must
originate from year 2018 in order to proceed further. We will add another
header Date that provides
the information about when the request was generated. Use
"Date": "Tue, 15 Nov 2018 12:45:26 GMTto set date back in 2018 and make the request. -
Now the response will present us a new heading that says: I don't trust users who can be tracked. This message referring to
Do not trackDo not track
request. So the server won't allow us until we enforce do not track and that's
exactly what we should do. Header named DNT is used for this purpose. By adding
DNT": "1"In HTTP request, we are notifying the web server that we have do not track enabled. Make the request and check the response. -
There will be another heading that say: This website is only for people from Sweden. Now if you paid attention to the previous requests, you can easily figure out that the HTTP request must originate from Sweden in order to
proceed further. When a request goes through multiple proxies, each proxy server
adds its own IP address in the X-Forwarded-For header and pass the request to the destination. Luckily, we can easily manipulate this header from the client side and make the web server look like the request comes from
Sweden. Add
"X-Forwarded-For": "103.57.72.55"header and value (which is an IP address belonging to Sweden location). Now make the request and check the response again. -
Now the heading changed again and says: You're in Sweden but you don't speak Swedish?. To manage this problem, we have a
Accept-Language header used to let
the web server know what language is preferred by the client for HTTP response. By
adding
"Accept-Language": "sv"In the HTTP request, we are notifying the web server that we know Swedish language and the HTTP response should be (if available) in this particular language. sv is language code for Swedish language. Now make the request to server and let's see what comes this time in the response. -
And this time we got the heading: What
can I say except, you are welcome. below that you can find your flag
picoCTF{http_h34d3rs_v3ry_c0Ol_much_w0w_0c0db339}to complete the challenge.
The process of finding flag in this challenge will be easy once you know about HTTP request manipulation. The method of altering the HTTP requests is widely used in web task automation. Check out RFC 2616, which is also provided in the challenge hint, to know more about HTTP headers.
login
My dog-sitter's brother made this website but I can't get in; can you
help?
https://login.mars.picoctf.net/
Like other challenges, this one does not provide any hint. Just one comes up with a challenge link that requires a username and password in order to get the flag. If you have paid attention to the previous challenges, you will get the idea that It's always best to check what files are being served by the server to the client.
In this case, along with CSS files, there is a javascript file index.js that is being served by the web server. If you know a little bit about character decoding, you may spot What's going on in the javascript file by just having a look at it.
There is this cGljb0NURns1M3J2M3JfNTNydjNyXzUzcnYzcl81M3J2M3JfNTNydjNyfQ random value in the javascript file that does not make sense but it surely looks encoded. So the first thing I did was try to decode it using base64 mechanism. Use the below command in Linux terminal:
echo "cGljb0NURns1M3J2M3JfNTNydjNyXzUzcnYzcl81M3J2M3JfNTNydjNyfQ==" | base64 -d
The output will be picoCTF{53rv3r_53rv3r_53rv3r_53rv3r_53rv3r} which
is the flag for challenge.





Good explanation. Will you update the article for more challenges ?
Reply
Sign up or Login to reply a comment
will update soon