Since the boom of the internet, securing online presence has been one of the toughest things to do. With the rise of better security and cyber awareness, threat to safeguarding one's online presence remains the same if not more. Every internet connection in the world is assigned an IPv4 or IPv6 address which is the online identity of that connection owner. These IP Addresses are assigned by the ISP (Internet Service Provider). In this article, we'll talk about some of the key factors that you must consider or implement to secure your public IP address.
VPN
When it comes to anonymity, VPN is the most effective method to secure your online activity and hide your public IP address. VPN is a Virtual private network that encrypts your internet connection traffic and routes it through a dedicated server that is located in another location (anywhere in the world).
Whenever you visit any website on the internet, your request will go to your VPN server first, and from there it'll be forwarded to the website that you requested. The request received by the website will contain the IP address of VPN server. This way you can mask your public IP address and encrypt the internet traffic using VPN.
Effectiveness of a VPN depends on the VPN provider. There are so many VPN providers in the market and each of them has their policies and regulations. Below are some of the key factors that you must be aware of before choosing a VPN:
- VPN only matters if the VPN provider has strict no-logs policy, which means they don't keep the record of your online activity.
- Never use VPN from an unreliable and untrusted VPN provider. Use only reputable VPN to stay on the safe side. It may not be cheap but It'll be more secure and privacy centered.
- Many VPN providers have a history of selling user data. Stay away from these types of VPN providers.
- If you value your freedom and privacy, always check the privacy rules of the country where your VPN server is located.
It is recommended to use VPN from a reputable VPN provider while keeping the above points in mind. However, If you have trust issues and you think everyone is trying to sell you out, you might need to look for the alternative method, which is to set up your own VPN server in the appropriate location.
Check the above article to set up your own VPN server in the cloud where you'll be the one in control of all of your internet traffic.
Proxy
A proxy server acts as an intermediary between your device and the internet. It forwards your internet traffic through its IP address, hiding your original IP address. Unlike VPN, traffic between your device and the proxy server is not encrypted. If someone is sniffing your network traffic, then that person can see your network traffic because there is no encryption on the data packets. Proxy servers are useful when the goal is to hide the IP address only, without any encryption of traffic.
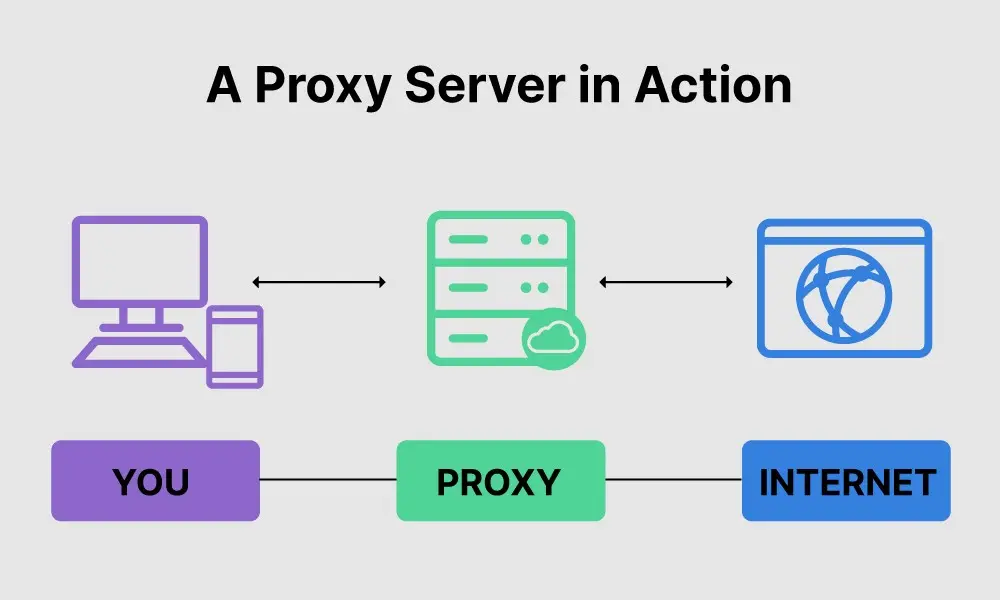
When you send a request to access a website or service, the request is first sent to the proxy server, which then forwards the request to the destination server on your behalf. The response from the destination server is sent back to the proxy server, which in turn sends it back to your device. There are both free and paid proxy servers available. You might lack speed, security, and reliability when using free proxy servers.
Tor network
Tor is a free open-source software that helps in protecting your online privacy. Tor (The onion router) is a network of multiple volunteer-operated servers that are used to route internet traffic and mask the original identity of the user. It's slow and used by individuals who are seeking strict privacy like journalists and whistleblowers.
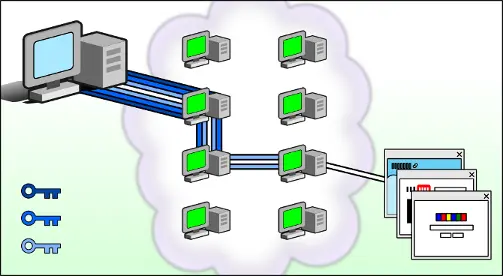
When using Tor network, your internet traffic is encrypted and routed through randomly selected Tor nodes. Working of the tor network is as below:
- The entry node is where your internet traffic enters the Tor network. It knows your IP address and, the IP of the next node, but not the destination's IP address.
- Middle nodes only know the IP address of Its previous and next node, not the source or the destination.
- The Exit node is where your internet traffic exits the Tor network. This node knows the destination IP address but not the source IP address.
Therefore even if your network is compromised, an attacker can never know both source and destination IP address. It's important to note that while Tor provides a high level of anonymity, it is not foolproof. Users are advised to other necessary measures and avoid exchanging sensitive information using Tor network.
One of the easiest ways to access the Tor network is by using Tor browser which is the official and recommended way of access. If you want to deep dive into the world of anonymity, check Torproject website and their blog posts.
Public Wi-Fi
This is the least secure way to hide your IP address and secure your privacy. When you are connected to a public Wi-Fi network, the source IP address of your internet traffic will be the IP address of public Wi-Fi. This way you can utilize the public Wi-Fi network and hide your IP address.

But most of the public Wi-Fi's are unsecured. If an attacker is connected to the same public Wi-Fi network then he can sniff the network and see all your internet traffic. Though traffic might be encrypted still he can see much valuable information to construct and launch another type of attack on your system. Which is why It's not recommended because the risk is too high.
Conclusion
Choosing the right method to hide your IP address depends on your specific needs for security, privacy, and performance. VPNs offer a good balance of security and speed, while Tor provides strong anonymity at the cost of slower speeds. Proxies and public Wi-Fi networks can be useful for basic privacy needs but may not offer the same level of security and privacy as VPNs and Tor.